Summary
This module covers common vulnerabilities and misconfigurations regarding Authentication that could be leveraged to gain unauthorized access to a web application. Specifically, in this module, we will cover:
- An overview of authentication methods
- Common protection mechanisms and possible bypasses
- Attacks against login processes
- Attacks against credential handling
CREST CPSA/CRT-related Sections:
- All sections
CREST CCT APP-related Sections:
- All sections
CREST CCT INF-related Sections:
- All sections
This module is broken down into sections with accompanying hands-on exercises to practice each of the tactics and techniques we cover. The module ends with a practical hands-on skills assessment to gauge your understanding of the various topic areas.
As you work through the module, you will see example commands and command output for the various topics introduced. It is worth reproducing as many of these examples as possible to reinforce further the concepts presented in each section. You can do this in the Pwnbox provided in the interactive sections or your virtual machine.
You can start and stop the module at any time and pick up where you left off. There is no time limit or "grading," but you must complete all of the exercises and the skills assessment to receive the maximum number of cubes and have this module marked as complete in any paths you have chosen.
The module is classified as "Medium." Still, it assumes a working knowledge of how web applications and HTTP work, the Linux command line, basic Python and PHP scripting, and an understanding of information security fundamentals.
A firm grasp of the following modules can be considered prerequisites for successful completion of this module:
- Linux Fundamentals
- Web Requests
- Introduction to Web Applications
What is Authentication
Authentication is defined as the act of proving an assertion. In this module's context, which revolves around application security, authentication could be defined as the process of determining if an entity (a user or an automated application) is who it claims to be.
The most widespread authentication method used in web applications is login forms, where a user enters their username and password to prove their identity. Login forms can be found on websites such as HTB Academy and Hack the Box to email providers such as Gmail, online banking, members rewards sites, and the vast majority of websites that offer some service. On HTB Academy, the login form looks like this:
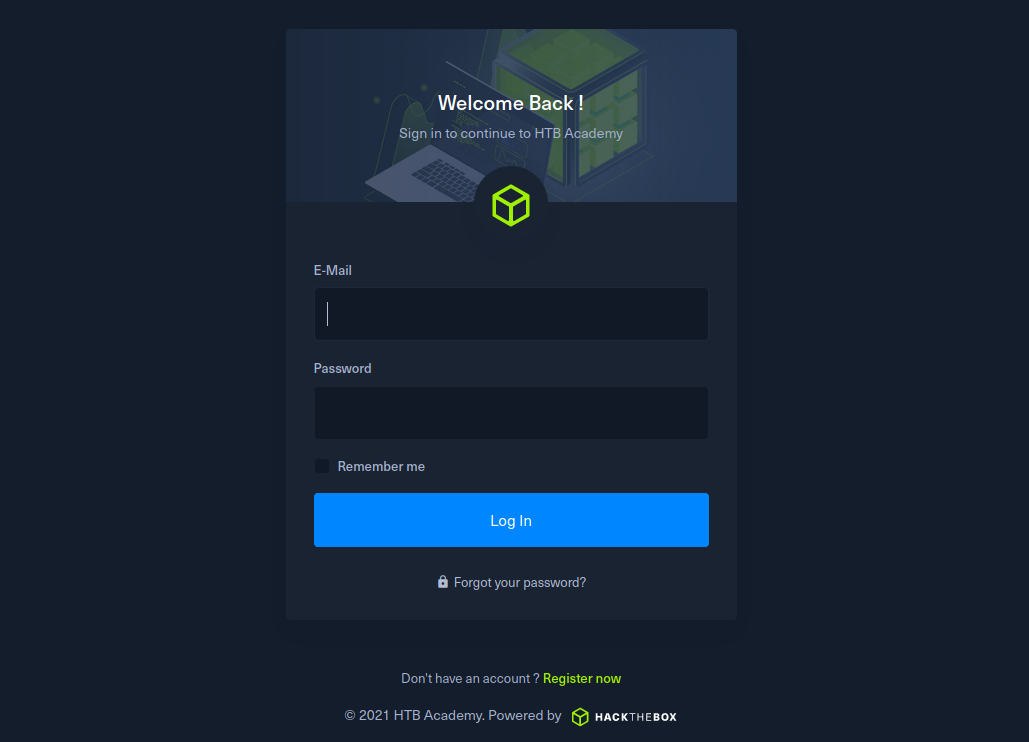
Authentication is probably the most widespread security measure, and it is the first line of defense against unauthorized access. While it is commonly referred to and shortened as "auth," this short version is misleading because it could be confused with another essential security concept, Authorization.
Authorization is defined as the process of approving or disapproving a request from a given (authenticated) entity. This module will not cover authorization in-depth. Understanding the difference between the two security concepts is vital to approach this module with the right mindset.
Assume that we have encountered a login form while performing a penetration test for our Inlanefreight customer. Nowadays, most companies offer certain services for which their customers have to register and authenticate.
Our goal as third-party assessors is to verify if these login forms are implemented securely and if we can bypass them to gain unauthorized access. There are many different methods and procedures to test login forms. We will discuss the most effective of them in detail throughout this module.







